In today’s interconnected world, the convergence of cyber and physical security has become increasingly critical, particularly for high-profile individuals. The recent breach of Gravy Analytics’ geolocation data highlights the emerging threat of geolocation vulnerability and its potential impact on physical security. High-profile individuals are now more than ever reassessing the extensiveness of their personal security measures, especially in the aftermath of incidents such as the UnitedHealthcare CEO shooting. This article aims to shed light on these vulnerabilities, emphasizing the importance of understanding one’s digital footprint and implementing proactive measures to mitigate risks.
Malicious actors targeting geolocation data for criminal or wartime exploitation present a significant threat to high-profile individuals. The ability to track precise real-time locations makes these individuals vulnerable. Integrating digital and physical security measures enhances protective strategies, promoting a proactive approach rather than a reactive one.
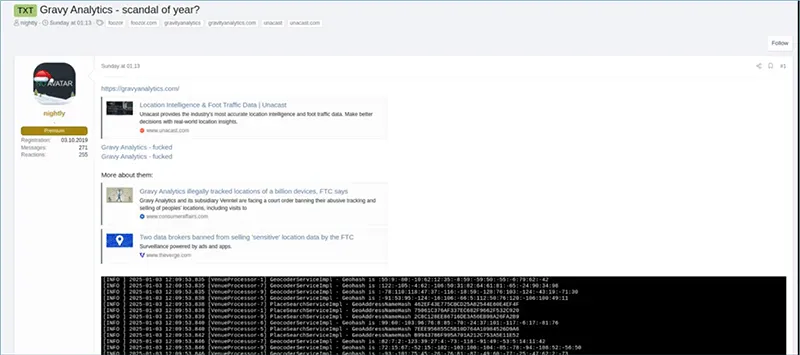
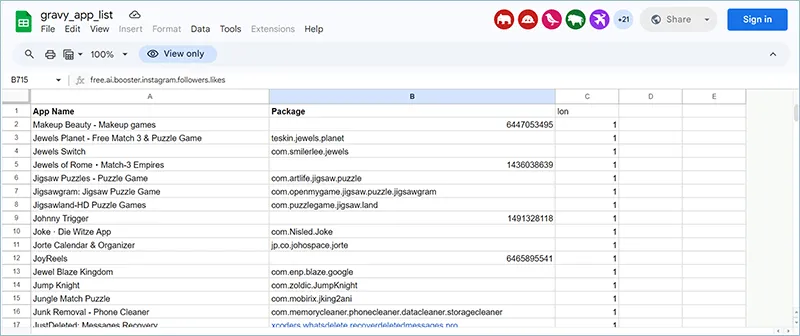
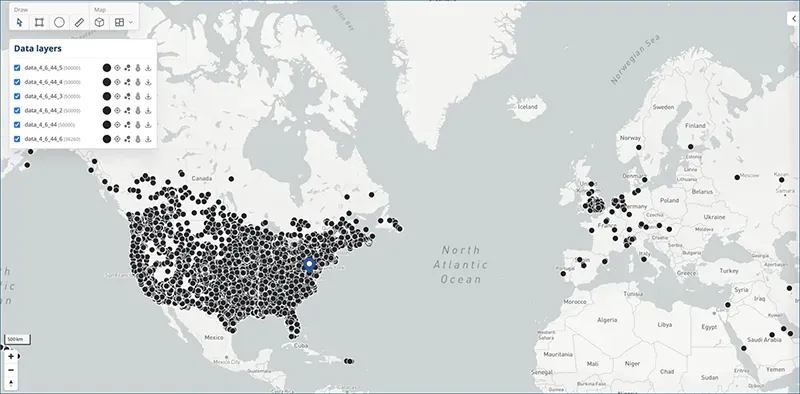
These digital issues are significant and ongoing. In January 2025, Gravy Analytics experienced a major breach that resulted in the compromise of its geolocation data and internal database. Since June 2011, Gravy Analytics has been collecting data and monitoring over a billion mobile devices daily. While geolocation data is intended to enhance convenience and enjoyment, the hack raises concerns about the potential misuse of compromised data by malicious actors to target high-profile individuals. Gravy Analytics is known as one of the largest providers of real-world location intelligence for business and advertising services. Its intelligence is used by commercial clients and U.S. government agencies such as the IRS, FBI, and U.S. Immigration and Customs Enforcement.
In recent years, geolocation technology and tracking incidents resulting in legal and ethical controversies have repeatedly made headlines. The proliferation of geolocation technology on mobile devices has led to costly and deadly incidents for militaries, intelligence services, and law enforcement agencies worldwide. The Gravy Analytics incident is one of many stark examples of risks and impacts executives and other high-profile individuals are facing when they have an exposed digital footprint. Other incidents include:
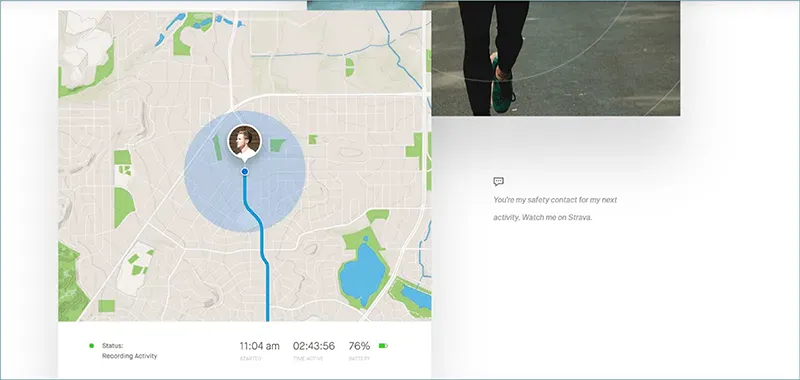
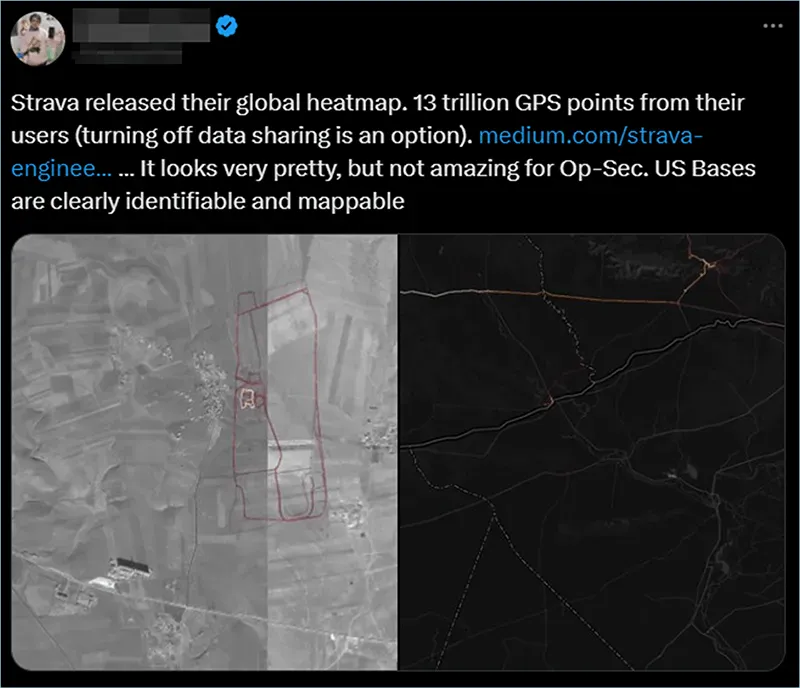
- The 2017 Strava Breaches
This popular fitness app faced scrutiny for its invasive tracking features that led to military security breaches and deaths in November 2017. Strava had an estimated 95 million active users in 2021.
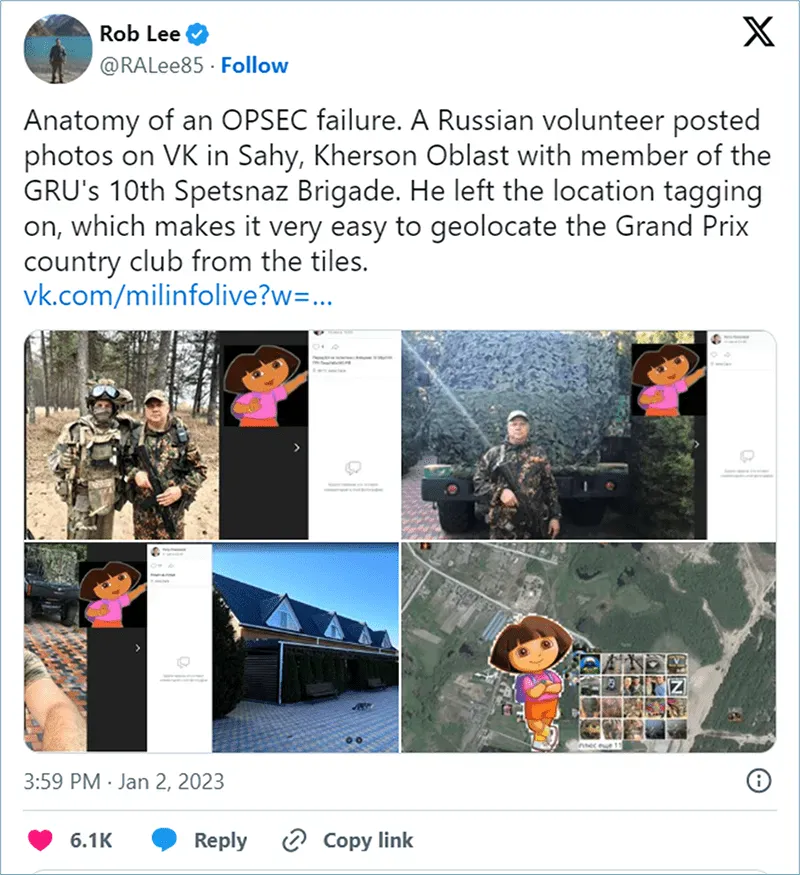
- The 2022 Ukraine-Russian Conflict
This conflict has highlighted multiple instances of social media, popular dating apps, and mobile app tracking features being used with deadly consequences, with victims becoming targets of aerial bombardment.
- The 2024 Paris Olympics
The threat actor Zeus launched a doxing campaign on social media platform Telegram against Israeli athletes. The threat actor stalked the Israeli team’s social media accounts for locations and incited physical violence against them.
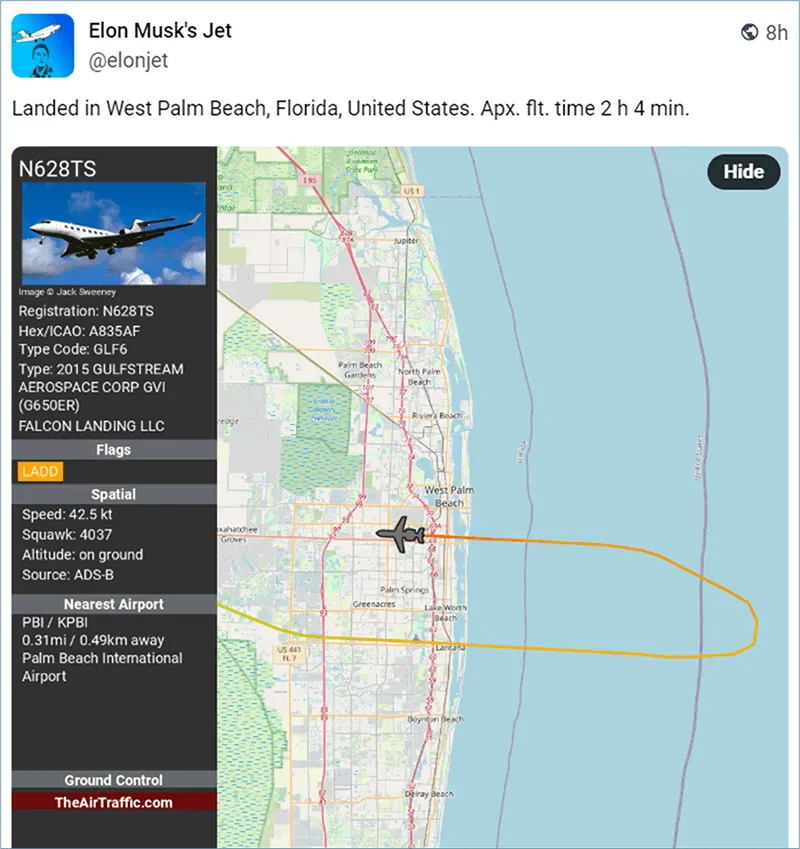
- U.S. Federal Air Tracking
Regulations allow for high-profile individuals such as Elon Musk and Mark Zuckerberg to be tracked through the movements of their private jets.
Mitigation Strategies
While we enjoy the benefits that mobile apps bring to our lives, being aware of the vulnerabilities, understanding your personal digital footprint, and knowing what can be done to minimize risk are prudent security considerations and good first steps toward having mitigation strategies to manage these threats.
- Management of Digital Footprint
By understanding an individual’s digital footprint, one can see who and what is vulnerable. Mitigating measures to protect privacy include limiting information on social media accounts, enabling privacy settings when available, using caution when accepting follow requests from other users, and turning off all location features. Professional monitoring services are available that are aimed at removing personally identifiable information (PII) from open-source and public-record websites.
- Threat Assessment
Capabilities exist to assess risk and identify and evaluate potential threats based on the individual’s profile, location, activities, and current geopolitical situations. Baseline assessments, coupled with a persistent monitoring effort, identify points of intervention where a threat actor might communicate their intentions so that proactive measures can be taken.
- Physical Security
Digital protective intelligence assessments are intended to support the decision-making of executives and their protection services. When determined necessary, physical security controls can be implemented, including access control, perimeter security, surveillance systems, and secure transportation routes or arrival and departure areas.
- Behavioral Profiling: Enhanced, Proactive Victim Selection and Victimology Analysis
Behavioral profiling is a critical component in understanding the threats and risks posed to executives by offenders who use cyber technology to facilitate physical harm. By analyzing digital footprints, online discourse, and threat actor behaviors, profiling helps identify patterns of intent, escalation, and modus operandi. Threats are assessed through behavioral indicators to determine the likelihood of real-world action. This proactive approach enhances executive protection by anticipating, mitigating, and neutralizing emerging threats before they manifest into physical danger.
Behavioral profiling also augments threat assessment and risk management with deep, proactive cyber victimology and cyber victim selection assessment. Cyber victimology analysis plays a crucial role in modern threat assessments by identifying how individuals, particularly high-profile executives, may be targeted based on their digital exposure, behavioral patterns, and vulnerabilities. Attackers often use mobile advertising technology, geolocation data, and publicly available personal information to conduct reconnaissance, predict routines, and exploit security gaps. By analyzing past victimization patterns, digital footprint exposure, and attacker methods, cyber victimology helps assess the likelihood and severity of targeted threats. This proactive approach informs executive protection strategies, enabling organizations to mitigate risks by reducing digital exposure, implementing stronger countermeasures, and pre-emptively identifying potential aggressors before threats escalate into real-world harm.
Similarly, cyber victim selection assessment is a strategic process to assess how threat actors are identifying and targeting individuals based on their digital exposure, behavioral patterns, and perceived vulnerabilities. High-profile executives are particularly at risk, as attackers exploit mobile advertising technology, geolocation tracking, and publicly available data to map routines, assess security weaknesses, and determine the most opportune moments for violent engagement. Factors such as online presence, personal data leaks, and corporate affiliations influence the victim selection process—making digital footprint management and mitigation critical to executive protection. By understanding how attackers profile and select their victims, organizations can implement targeted risk mitigation strategies, reduce exposure, and disrupt threat actor reconnaissance efforts before an attack.
Facts of the Hack
Gravy Analytics, headquartered in One Loudoun, Virginia, is a real-world location intelligence provider for business marketers. After merging with Norwegian location tracking company Unacast, it became the leading provider of its kind.
In January 2025, a threat actor identified as “Nightly” claimed to have exfiltrated 17 TB of data from the company’s network, originating from over 12,373 brands. Following is a timeline of the breach and related details.